
This service is primarily geared towards companies that already have an internal IT Infrastructure in place to handle the day to day; however, need to have their IT Security Program augmented to include Firewall, Advanced Endpoint Protection, Security Operations, and Remote Management and Monitoring.
Our service will give you peace of mind knowing that your company is meeting its compliance and risk goals as well as having extra people on hand as needed to be proactive in addressing not only your Cyber Security needs, but your IT Service and Asset Management as well (ITSM/ITAM).
We can use a Hybrid Environment to describe a use case for this service. A company has On-Premises servers for Active Directory and other services and multiple workstations, printers, etc. The company also uses Microsoft Azure services to connect apps, containers, and services.
Firewall Technologies
Using our Firewall Technologies and Advanced Technicians, we conduct a deep dive into those areas of a network infrastructure that needs to be addressed for optimization of security and reducing the attack surface of your networks. We then build security based around the services on that network. For example, if your VoIP system is on a given network, it only needs access to those servers and phones to perform the function of staying up to date, send phone configs, and certain features as needed. This reduces the attack surface by limiting the network to only communicate with what it needs to perform its function. This also allows for the Firewall(s) to do the heavy lifting for the infrastructure by preventing attacks and potential breaches from getting on the network in the first place. We are proud to Partner with Arista Edge to provide this service and it is interesting to note, that one customer with around 75 nodes, we prevent more than 2 million attacks and threats per month. That is almost 27 thousand prevented attacks/threats per device on the network each month!
Andvanced Enpoint Protection
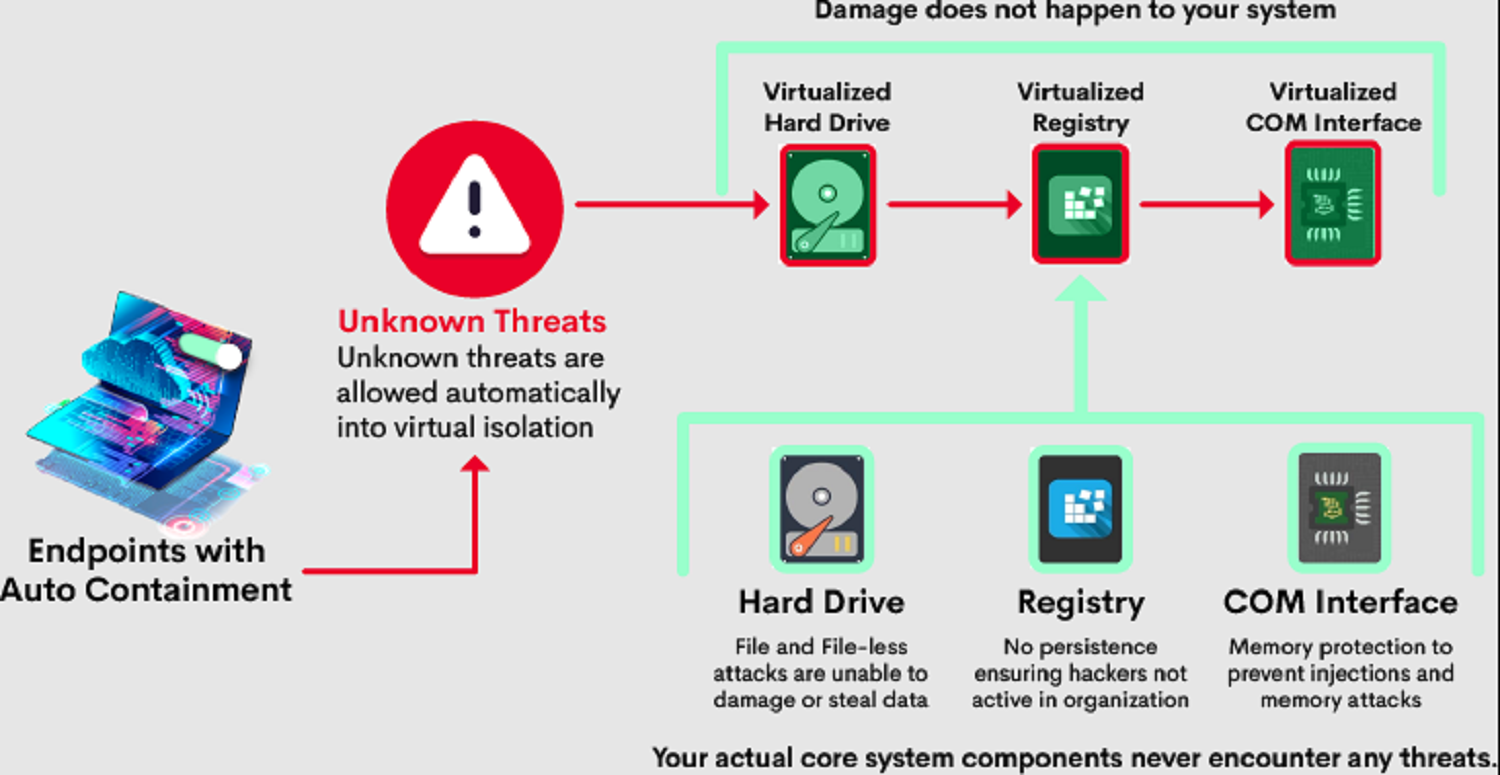
Our Advanced Endpoint Protection (AEP) is fully customizable and can be tailored to fit your needs. Our AEP is based on Zero-Trust principles that uses Auto-Containment and analyzes each process and steps taken to ensure that what happens on your workstations and servers are correct and Malware free. Using our AEP along with our Communication Client also provides the ability to provide or prevent actions on the workstation or server. The Remote management and Monitoring (RMM) capability is provided alongside our AEP allowing for us to set up for events such as automated recurring server/workstation patching (on your downtime), proactively respond to server downtimes, security threats including ransomware, and can even control what removable devices may be used within the environment. This is just a brief description of the capabilities and just the tip of the Iceberg.
Security Operations Center
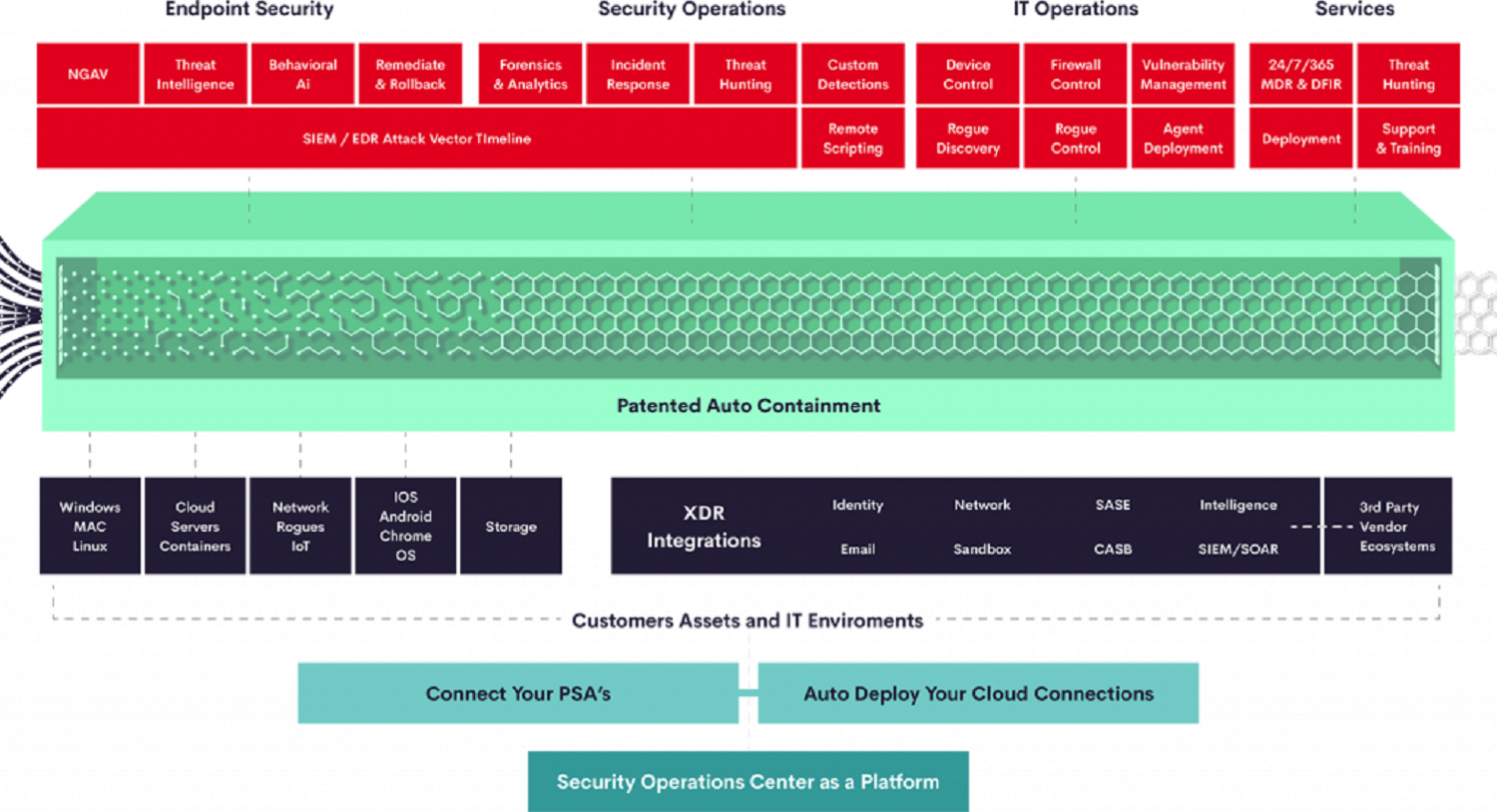
Tying this in with our Security Operations, you get additional peace of mind in that your networks, servers, and workstations not only receive 24/7 protection from the Firewall and AEP; however, receive an additional 24/7 monitoring for Security Incidents with a highly proactive response capability. Our Security Operations actively searches for incidents on Workstations and Servers, Networks, Cloud Environments, and Websites to keep you safe and secure. We are Proud to partners with XCITIUM to provide these capabilities.
Success with your IT Security Program is our mission, and we are happy to work with you towards meeting these objectives. We make it a point to provide these services at our best affordable rates to meet your business needs. Please contact us to request a demo and get pricing.
Key Features
- Low Startup Cost.
- Highly Scalable.
- 24x7/365 Monitoring.
- Easily integrates with our Managed IT Services Platform and Service Desk.